What Step Is Part of Reporting of Security Incidents
Definitions Information Security Incident. BExclude notation of incident from the patients medical record.
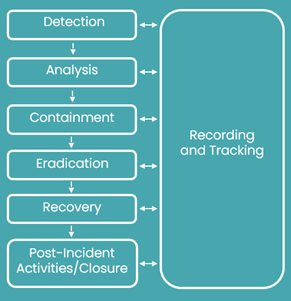
Incident Response Policy And Procedure Icims
Step 2 Complete Security Incident Report.

. Security incidents are on the rise coming from a multitude of directions and in many guises. AReport disclosure to all patients. If you see something say something is the motto of the Department of Homeland Security.
Step 3 Receive incident determination from CDA Program Manager. Technology Examination Handbook IT Handbook on Information Security management should define thresholds for reporting security incidents internally and develop processes for when the institution should notify its regulator of incidents that may affect the institutions operations reputation or sensitive customer information. SECURITY INCIDENT REPORTING PROCEDURES ReportallsuspectedorconfirmedSecurityIncidentsImmediately TheUniversityofMassachusettsMedical.
The Importance of Security Incident Reporting. The University of Massachusetts Medical School UMMS Information Security IT Help Desk should be notified immediately of any suspected or confirmed Security Incident involving UMMS Technology Assets or UMMS information in electronic or hardcopy format. Its a motto that is also highly relevant to ensuring that our systems and data are secure.
Your reporting process should include accommodation for regulatory reporting escalations. Security Incident Reporting Procedures Step 1 Report Crime to local law enforcement if required. Information security incident refers to an adverse event in an information system network andor workstation or the threat of the occurrence of such an event.
While internal reporting of security incidents is an inherent part of security incident policies and procedures the Security Rule generally does not require a covered entity to report incidents to outside entities. CNotify Business Associates and Trading Partners of the breach. When security incidents occur documentation is required for compliance.
Finance where operators need to report incidents to regulators. The Security Officer for the organization is the individual responsible for this documentation whether in an electronic or written format. The information security incident reporting form is an important first step in handling information security incidents in a coordinated response.
The security incident report needs to contain certain information to meet compliance. Reporting Critical Cyber Security Incidents. Report all suspected or confirmed Security Incidents Immediately.
The update to FISMA is an important first step toward solving supply chain security problems exposed by SolarWinds rather than simply identifying them. -What step is part of reporting of security incidents. Be sure to have your lines ready in case they contact.
Incident reporting should be part of a bi-directional flow of information where providers report about security incidents to authorities and authorities feedback common threats and common issues to the cloud providers so they can improve security and resilience. It is best to. The next step is arguably the most important and official of all the steps and ensures that the immediate manager and any authorities are informed about the incident.
Analysts create an incident ticket document initial findings and assign an initial incident classification. Does the reported incident meet the criteria for. Quantify Significant Cyber Incidents.
Step 4 Reporting person coordinates with. Detect potential security incidents by correlating alerts within a SIEM solution. Incident reporting plays an important role in these efforts as it contributes in improving stakeholders knowledge of the actual security problems at stake.
This in-depth look at the nature of the threat and the best ways to respond to it now is essential reading for any security professional. Activate a Computer Security Incident Response Team CIRT to investigate assess the damage collect evidence report the incident and perform recovery procedures. Identify potential security incidents through monitoring and report all incidents.
A significant impact is one where both. Respond to the incident by containing investigating and resolving it. As part of the EO and existing FISMA statute Federal Civilian Executive Branch FCEB agencies are required to report significant breaches.
Security incident report Contact information. Once youve double-checked the security incident report youve written and youre confident that everything in the report is true and correct it is now time to submit your report to the investigator or to the authorities so they can begin their investigation and provide their appropriate recommendation report and feedback. Incident Response Step 2 Response.
An effective incident reporting system contributes to the collection of reliable and up-to-date data on information security incidents and ensures. Assess identified incidents to determine the appropriate next steps for mitigating the risk. However 164314 a 2 i C and b 2 iv require contracts between a covered entity and a business associate and plan documents of a group health plan.
You need to make sure that it is immediately reported so that people can remain protected from any knock-on damage that might occur. If you become aware that a critical cyber security incident has occurred or is occurring AND the incident has had or is having a significant impact on the availability of your asset you must notify the Australian Cyber Security Centre ACSC within 12 hours after you become aware of the incident. This helps to limit damage the quicker the.
The bulk of the effort in properly. In order to have an effective cyber security program you need eyes and ears everywhere. Security Incident Reporting Procedures.
IDS Security Services must provide clearance to reconnect or use a system that has been part of an incident investigation and recovery suspected or confirmed. Users reporting a security incident will be informed of the resolution or outcome of the incident response and recovery after all investigations have been completed.
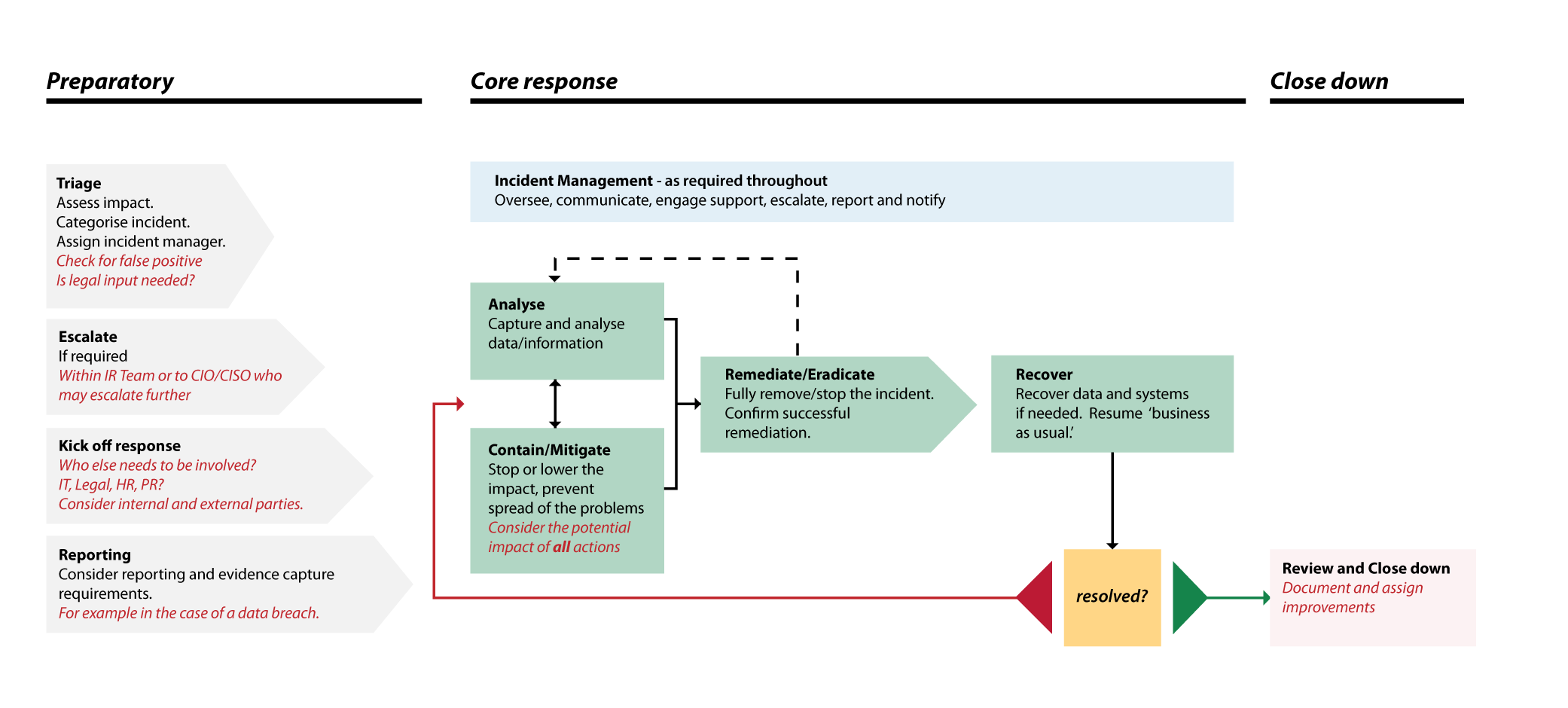
Plan Your Cyber Incident Response Processes Ncsc Gov Uk
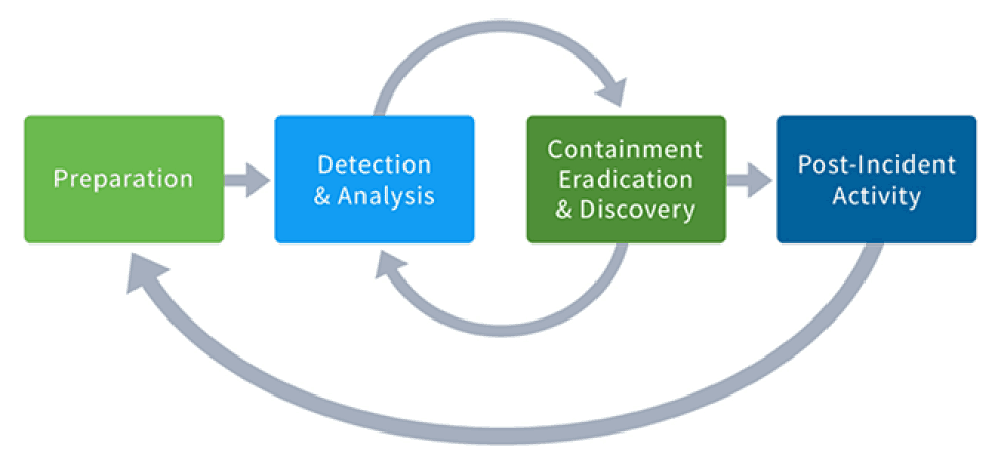

No comments for "What Step Is Part of Reporting of Security Incidents"
Post a Comment